Application is encrypted during protection. It is also distributed in encrypted state so there is no easy way for malicious patching of protected application. Decryption process is done automatically by our protection code once the application is loaded into memory.
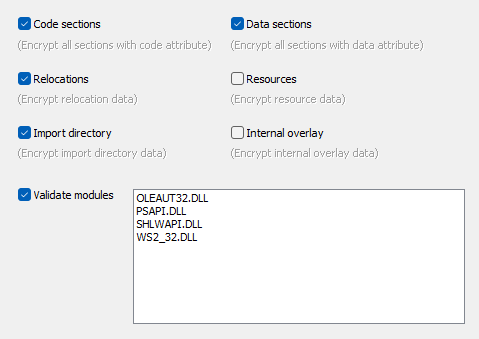
Encryption options
1. Code sections (sections with code attribute set)
2. Data sections (sections with data attribute set)
3. Relocations (relocations data)
4. Resources (resource data)
5. Import directory (import directory data)
6. Internal overlay (internal overlay data - data attached at the end of file)
Validate modules option
Select this option to enable Integrity validation checks for specific imported modules by selecting modules to be validated from the list of imported modules.
Protection code will save information about these modules during protection process into protected application. In this way protection code will be able to check integrity of these modules on remote computer once they are loaded by protected application into memory and prevent replacing of these modules with different or even malicious versions of these modules.